Install once, monitor always — trusted for BFSI, defense, and secure datacenters.
The Case for On-Prem AI Monitoring
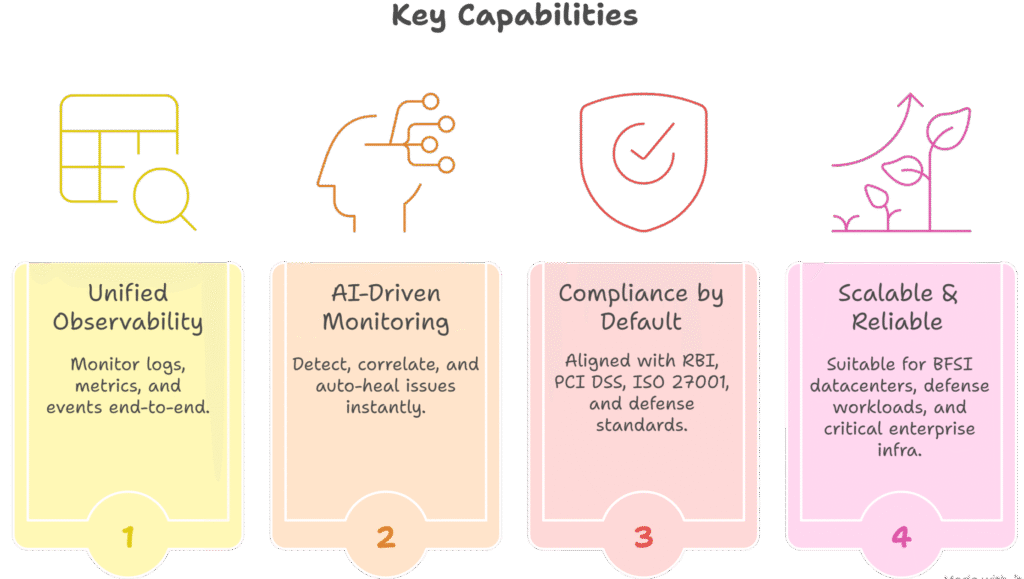
In industries like BFSI, defense, and government datacenters, cloud monitoring often fails to meet the strict demands of data sovereignty, regulatory mandates, and air-gapped environments. Sensitive workloads — from financial transactions to national defense operations — require monitoring that never lets data leave secure boundaries.
On-Prem AI Monitoring ensures security, compliance, and resilience by keeping all telemetry within enterprise control. It enables faster local intelligence, supports audit readiness, and remains reliable even in disconnected or hybrid environments, making it essential for mission-critical operations.
Key Capabilities
Proactive event correlation and self-healing automation for complex IT stacks.
The Case for AI-Powered RCA
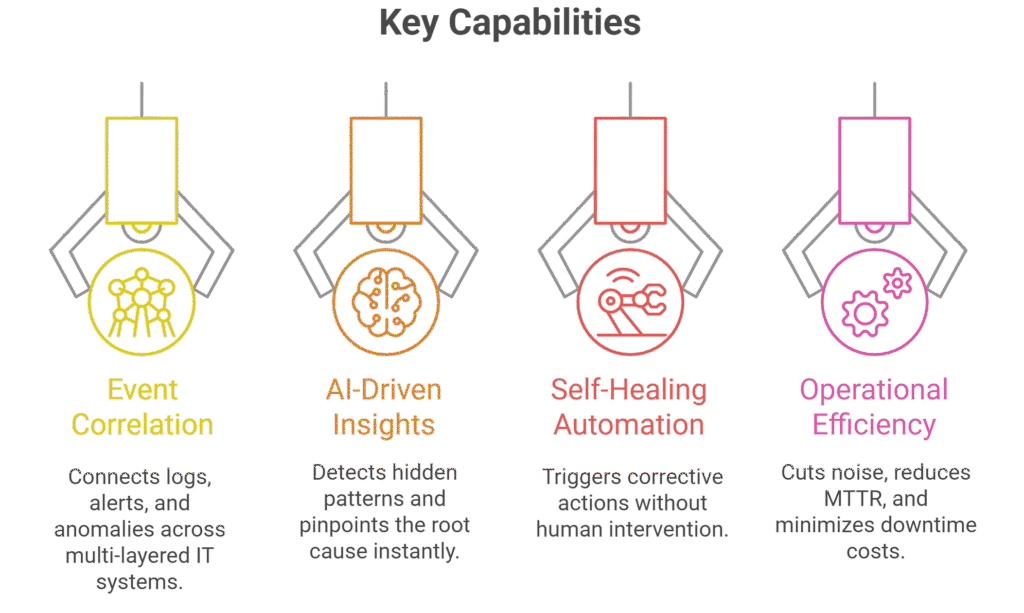
Modern enterprises run on heterogeneous IT environments — databases, applications, cloud, on-prem, and edge systems — each generating massive volumes of logs, events, and alerts. Traditional monitoring often overwhelms IT teams with noise, delaying incident resolution and increasing downtime costs.
AI-Powered Root Cause Analysis transforms this challenge by correlating events, analyzing anomalies, and identifying the true source of issues in real time. Instead of manual triage, enterprises gain automated insights and corrective workflows that reduce mean time to resolution (MTTR) and ensure resilience across complex infrastructures.
Key Capabilities
AI-Powered RCA: Faster Insights. Smarter Actions. Greater Resilience.
Supports RBI/NPCI compliance, policy enforcement, and audit workflows.
The Case for Compliance-Ready Infrastructure
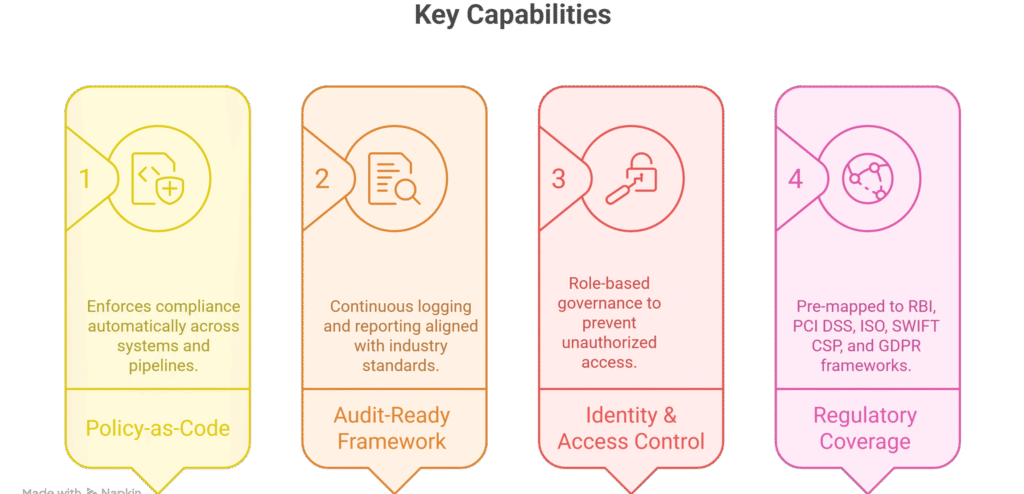
For industries like banking, financial services, and government enterprises, compliance is not optional — it is the foundation of trust. Regulations such as RBI, PCI DSS, ISO 27001, GDPR, and SWIFT CSP require strict controls across infrastructure, data, and operations. Traditional IT setups often treat compliance as an afterthought, leading to costly audits, penalties, and operational risks.
Compliance-Ready Infrastructure changes this by embedding governance, auditability, and policy enforcement into the core of IT operations. From access control to continuous monitoring, every component is designed to meet regulatory standards, ensuring enterprises stay audit-ready, secure, and resilient by default.
Key Capabilities
Compliance-Ready Infrastructure: Built for Trust. Designed for Assurance.
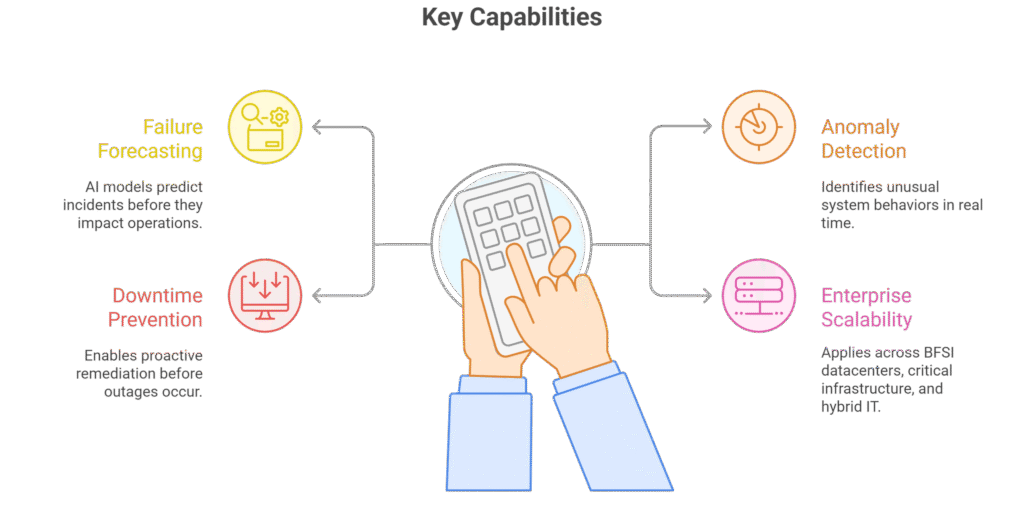
The Case for Predictive Analytics
Downtime is one of the biggest hidden costs in enterprise IT — impacting revenue, compliance, and customer trust. Traditional monitoring is reactive: teams only respond after an outage has occurred. In high-stakes environments like BFSI, telecom, manufacturing, and defense, this reactive approach is simply not enough.
Predictive Analytics introduces a proactive model. By analyzing historical patterns, system behavior, and real-time telemetry, AI models forecast potential failures before they happen. This allows IT teams to act early, schedule maintenance intelligently, and avoid unplanned disruptions — improving uptime and saving costs.
Key Capabilities
Predictive Analytics: From Reactive Monitoring to Proactive Resilience.
Intelligent alerts with automated remediation workflows.
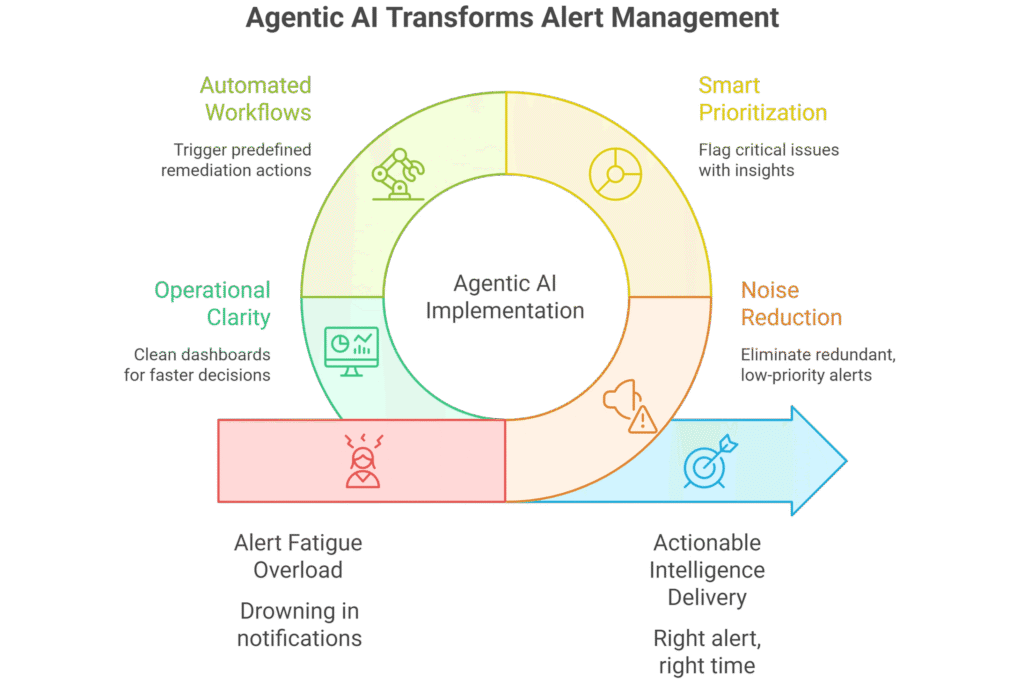
The Case for Agentic AI Alerts
Enterprise IT teams are drowning in alert fatigue — thousands of notifications across monitoring tools, many of which are redundant, low-priority, or false positives. This overload not only slows response times but also leads to critical incidents being missed.
Agentic AI Alert Intelligence solves this by filtering, prioritizing, and contextualizing alerts. Instead of overwhelming IT teams, it delivers actionable intelligence: the right alert, at the right time, with the right remediation workflow. Combined with automation and self-healing, it reduces noise, cuts manual effort, and ensures that critical issues are addressed immediately.
Key Capabilities
Agentic AI Alerts: From Noise to Actionable Intelligence.
Packaged for OEM bundling, managed services, and air-gapped environments.
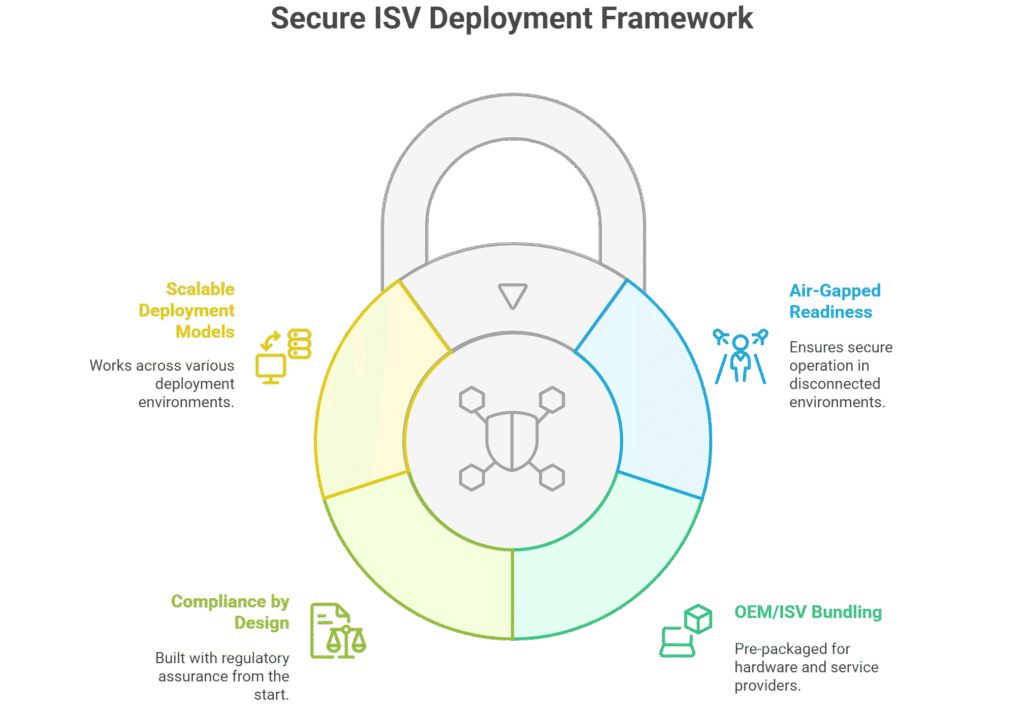
The Case for Secure ISV Deployment
Independent Software Vendors (ISVs) and OEMs face growing demand for secure, enterprise-ready deployments that can operate in air-gapped, compliance-heavy, and mission-critical environments. Traditional SaaS delivery often fails in these cases due to data sovereignty, regulatory restrictions, or infrastructure isolation.
Secure ISV Deployment provides a way to deliver hardened, packaged, and scalable AI-powered solutions that meet enterprise and government requirements. Whether for OEM bundling, managed services, or on-prem deployments, it ensures that software runs securely, integrates seamlessly, and scales without compromising compliance or resilience.
Key Capabilities
Secure ISV Deployment: Enterprise-Grade AI, Anywhere You Need It.